Restore conditional access policies from audit log
From time to time, I need to restore Conditional Access policies that have been deleted or changed. If you don’t have a backup of the policies, you can luckily use the audit logs to help you restore. Up until now I have just crawled my way through KQL queries to find the information I need, but a recent Entra ID preview feature allowing you to view each change as a colored diff gave me an idea. What if I could create a script to compare the policy at any point in time as far back as I store my audit logs? ...
Conditional Access - Deploying new policies using data
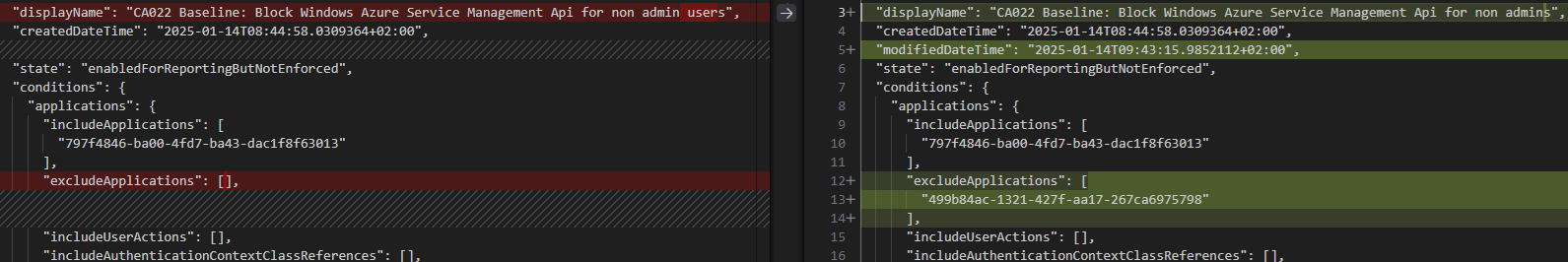
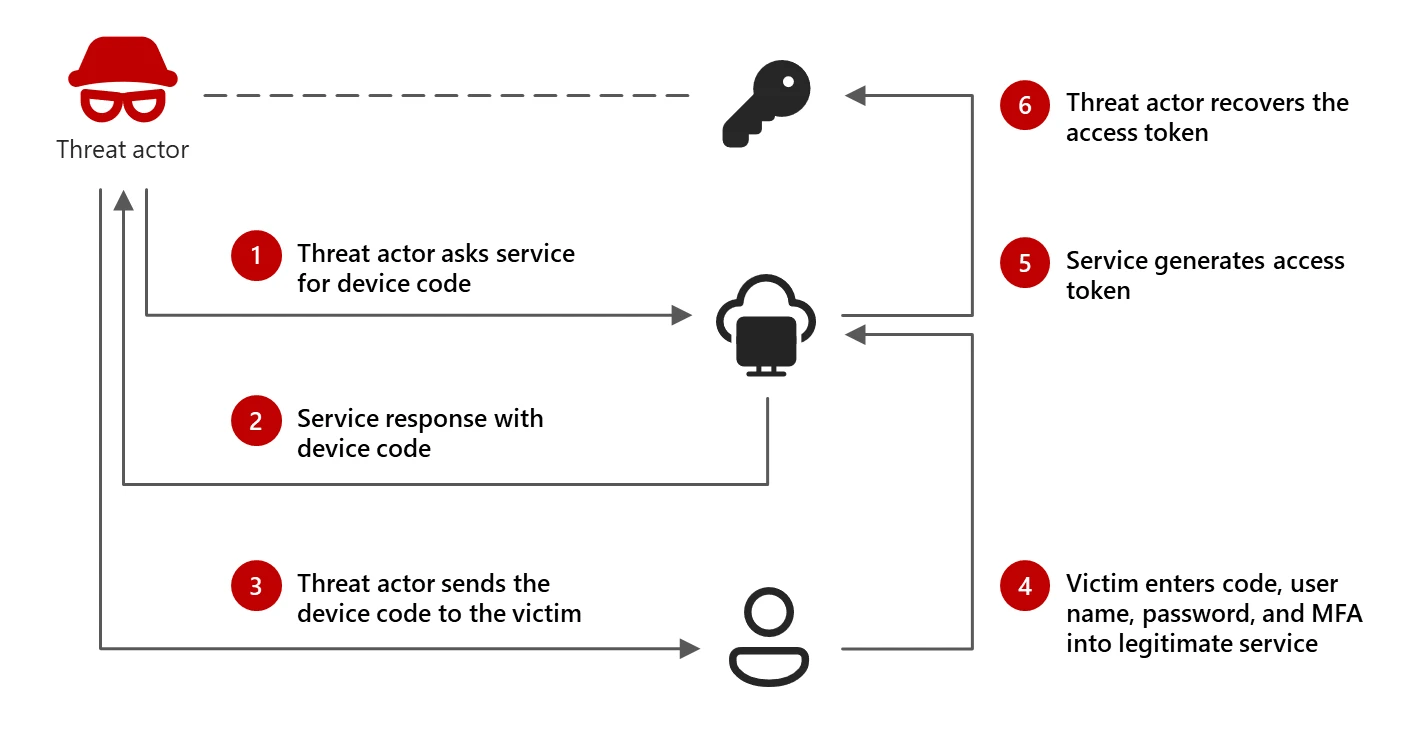
Image source: (Storm-2372 conducts device code phishing campaign) Last weeks device code phishing campaign conducted by “Storm-2372” forced many organizations to quickly implement countermeasures to block the attack. While I hope most organizations has already had the time to implement the necessary changes, I wanted to share a few tips on how to use data to target your deployment. Both for this specific campaign, but also for other similar controls. Conditional Access Conditional Access is a powerful tool to control access to your resources. It can be used to enforce MFA, block legacy authentication, or block access from certain locations. In this example, we want to block access to using the device code flow for all users. But what if you don’t know if device code flow is used in your organization today? Let’s dive into the data available to us to investigate. ...
Entra ID - Add permissions to Managed Identity
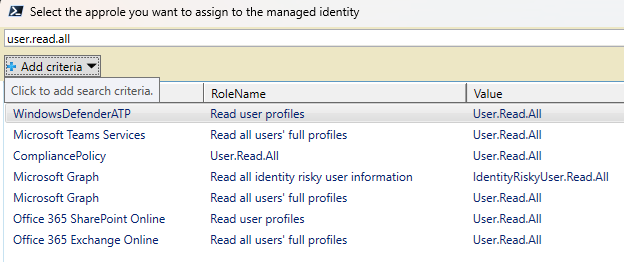
Adding permissions to Managed Identities in Entra ID is annoyingly complicated. To make the job easier, I created a short script that allows me to search through all possible permissions in a simple GUI. The script outputs the command needed to add the permission to the managed identity. If you feel confident, you can modify the script to run it directly. Connect-MgGraph -Scope Directory.Read.All, AppRoleAssignment.ReadWrite.All, Application.Read.All # Object ID of the managed identity, NOT application ID! $servicePrincipalId = "00000000-0000-0000-0000-000000000000" # Get all service principals in tenant. Lazy first version. This can be filtered down into the actual useful applications. $allServicePrincipal = Get-MgServicePrincipal -All $roles = $allServicePrincipal | ForEach-Object { foreach($r in $_.AppRoles) { [PSCustomObject]@{ AppId = $_.Id DisplayName = $_.DisplayName Id = $r.Id RoleName = $r.DisplayName Value = $r.Value } } } # List all roles and let the user select one (hit enter to continue in the gridview) $roles | Out-GridView -PassThru -Title "Select the approle you want to assign to the managed identity" | ForEach-Object { $chosenRole = $_ } @" To grant $($chosenRole.RoleName) ($($chosenRole.Value)) from $($chosenRole.DisplayName) to the managed identity with object ID $servicePrincipalId, run the following: `$params = @{ principalId = $servicePrincipalId resourceId = $($chosenRole.AppId) appRoleId = $($chosenRole.Id) } New-MgServicePrincipalAppRoleAssignment -ServicePrincipalId $servicePrincipalId -BodyParameter `$params "@ Link to script on GitHub: Add permissions to Managed Identity ...
Entra ID application permission report with usage
Enterprise applications and app registrations are two of the most dangerous things in Entra ID if managed incorrectly. They grant access to your data and resources, and if compromised, can lead to data breaches and other security incidents. Do you have control over all permissions granted over the course of your tenants lifetime? When was the last time you deleted stale permissions? Application permission report My collegue Sridhar linked me a PowerShell module called MSIdentity Tools, which contains a command called Export-MsIdAppConsentGrantReport. This command exports a report of all application permissions granted in the tenant, together with some additional helpful information related to risk. ...

SharePoint Advanced versioning
Is your company paying for extra SharePoint storage? Would you like not to? What is it? SharePoint and OneDrive automatically saves major or minor versions as you work, so there is a history of changes that you can access and revert to if needed. Microsoft recently started rolling out general availability of feature ID 145802: “SharePoint: Improvements for document library version history limits”. In simpler terms this means we now have an automatic way of thinning out the version history of files and documents in SharePoint Online. ...

Optimizing Microsoft 365 licensing. Part 2 - Data driven license optimization
This article will dive into license optimization. Which reports and measurements are available to us, and what are the important metrics to guide the decision on which license package a user needs? Ultimately, we want to use this information to reduce cost, but it can also help us to discover if we are uncompliant according to the license contract. If you haven’t already, I recommend reading through part 1 of this series to get a brief understanding of license profiles. I will be referring to some terms introduced there. If you are already familiar with Microsoft 365 licensing, then part 2 is the place to start. ...

Optimizing Microsoft 365 licensing. Part 1 - License basics
It’s that time of the year. You have one month before the yearly license numbers are due to be delivered to Microsoft. The questions have started pouring in. Can we make any savings? Are we utilizing all the features we have purchased? Do we have enough licenses for all our workloads? Are we even compliant? This guide focuses on the things I consider to be the most important when designing your license strategy. The main purpose is explaining the basics and setting the scene for part 2 and 3 where I will talk about investigating the data available to us, and how to automate most of the process. ...